20+ router firewall diagram
Routershow access-list Extended IP access list 101 10 permit tcp any any 20 permit udp any any 30 permit icmp any any. Feedback occurs when outputs of a system are routed back as inputs as part of a chain of cause-and-effect that forms a circuit or loop.

Features Overview Sonicwall Tz270 Wireless Ac Network Security Appliance 02 Ssc 2823
800M Integrated Services Router Choice of wireless WAN services and providers.

. BitTorrent clients are available for. Outlined correctly the firewall can help facilitate two separate connections on the wireless network. Session Initiation Protocol June 2002 Call.
The benefits of a VPN include increases in functionality security and management of the private networkIt provides access to resources. Open a TAC Case Online. A subnet named my-subnet-2 with primary range 1921680020 for your cluster nodes.
The radio frequency link establishes a connection to the switching systems of a mobile. Wed May 20 120600 2020 111 12121212 from 12121212 1111. The following diagram shows a.
The goal is to securely connect both LAN networks and allow full communication between them without. Your subnet has the following secondary address ranges. If the first element in the route set indicated a strict router resulting in forming the request as described in Section 12211 the procedures MUST be applied.
If you are looking for VIP Independnet Escorts in Aerocity and Call Girls at best price then call us. These are most commonly used to map human-friendly domain names to the numerical IP. The following diagram shows the connectivity requirements for AKS inferencing.
With the performance and security features of the Linksys cableDSL firewall router with 4-port switchVPN endpoint your network will take advantage of the Internet while keeping its data secure. HSRP Hot Standby Router Protocol is the Cisco proprietary protocol for providing redundancy in router networks. Choose a WiFiRanger indoor or outdoor router with an integrated LTE modem to take advantage of the Winegard.
NATing and Forwarding can be handled using iptables or via the iptables front-end utility like UFW. Black arrows represent actual communication and blue arrows represent the domain names. A call is an informal term that refers to some communication between peers.
When you sign up for TELUS internet you will receive a device called a gateway - a two-in-one modem router combo. The server will see that the DHCP request came from source subnet 1921681024 and will therefore assign an appropriate IP address from a configured IP pool scope within the. By configuring an ip helper-address 1010101 under interface Fe00 of Router A we tell the router to turn the DHCP broadcast into a DHCP unicast and send it to destination DHCP server 1010101.
Beratung und Erreichbarkeit Online-Antragstellung Servicetipps und vieles mehr. A virtual private network VPN extends a private network across a public network and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Coronavirus - Service und Informationen Die Corona-Pandemie bedeutet drastische Einschnitte in allen Lebensbereichen.
The Domain Name System DNS is the hierarchical and decentralized naming system used to identify computers reachable through the Internet or other Internet Protocol IP networks. VSAN overhead and NSX-T distributed router firewall and bridging overhead. 1520 SSD All product regions.
Standards Track Page 20 RFC 3261 SIP. The notion of cause-and-effect has to be handled carefully when applied to feedback systems. Both the branch routers connect to the Internet and have a static IP Address assigned by their ISP as shown on the diagram.
Show router bgp get router info bgp summary get router info bgp network. What Is Bridge Mode. The sequence numbers such as 10 20 and 30 also appear here.
WiFiRanger secures the local network of the router with a robust firewall which blocks suspicious or uninvited network traffic and connection attempts. Including vCenter Server VMware HCX NSX-T Data Center and vMotion functionality. Bridge mode is a feature that allows a user to shut off the router side of the gateway ie.
Connectivity for up to 20 users 880 3G Integrated Services Router. A mobile phone cellular phone cell phone cellphone handphone hand phone or pocket phone sometimes shortened to simply mobile cell or just phone is a portable telephone that can make and receive calls over a radio frequency link while the user is moving within a telephone service area. WiFi and use a 3rd party router in its place.
Site 1 is configured with an internal network of 101010024 while Site 2 is configured with network 202020024. Use Cloud NAT to create and configure a Cloud Router. Cloud NAT lets private clusters establish outbound connections over the internet to send and receive packets.
The previous ACLs are not supported in Security Appliance such as the ASAPIX Firewall. This router is compatible with Windows 95 98 NT 2000 Me and XP. All Linksys routers now include a special edition of Norton Internet Security.
BitTorrent is a communication protocol for peer-to-peer file sharing P2P which enables users to distribute data and electronic files over the Internet in a decentralized manner. This must be outlined carefully to address vulnerabilities that can lead to the theft of vital company information. Packages ranging from 1 GB to 20 GB with no throttling US.
The standard router redundancy protocol which is used by other vendors is VRRP Virtual Router Redundancy Protocol however Cisco has created its own proprietary protocol HSRP which works very well on Cisco routers. Dual Intel 18 core 26 GHz 39 GHz turbo Cascade Lake. Simple causal reasoning about a feedback system is difficult because the first system influences the.
The system can then be said to feed back into itself. TELUS currently only offers bridge mode on 3 gateway models - the T1200H T2200H. You may need to add entries for these hosts to your firewall or to your custom DNS server.
Visio Stencil 757 KB zip file Contact Cisco. For example you may be using a firewall to block network traffic. The firewall connection forms a significant core of the network diagram.
A WPA2 connection for work computers and an open. In a Local Area Network LAN all. Auf dieser Seite finden Sie alle Informationen der Deutschen Rentenversicherung die jetzt wichtig sind.
To send or receive files users use a BitTorrent client on their Internet-connected computerA BitTorrent client is a computer program that implements the BitTorrent protocol. The resource records contained in the DNS associate domain names with other forms of information. We wanted to see the full potential of the good old reliable 10G networking combined with a modern CPU.
CCR2116-12G-4S allows you to forget about CPU limitations in your setup. Aerocity Escorts 9831443300 provides the best Escort Service in Aerocity. Configure NATing and Forwarding on Linux Router.
Configure the packets received from router LAN interfaces enp0s8 and enp0s9 to be forwarded through the WAN interface which in our case is enp0s3iptables -A FORWARD -i enp0s8 -o. These are estimates for a standard three cluster configuration. Like its younger brother the amazing CCR2004 this router.
Add the entry for the access list 101 with the sequence number 5. Configure firewall policies to allow BGP TCP sessions to the loopbacks to be established.

Basic Routing Configuration Topology 1 Make Basic Ip Addresses Download Scientific Diagram
Prototype Of A Network Download Scientific Diagram

Top Countries To Work For Software Engineer Best Countries To Work In 2017 Highest Paying Countries For Software Engineer Programming Languages Coding Software

Community Gns3
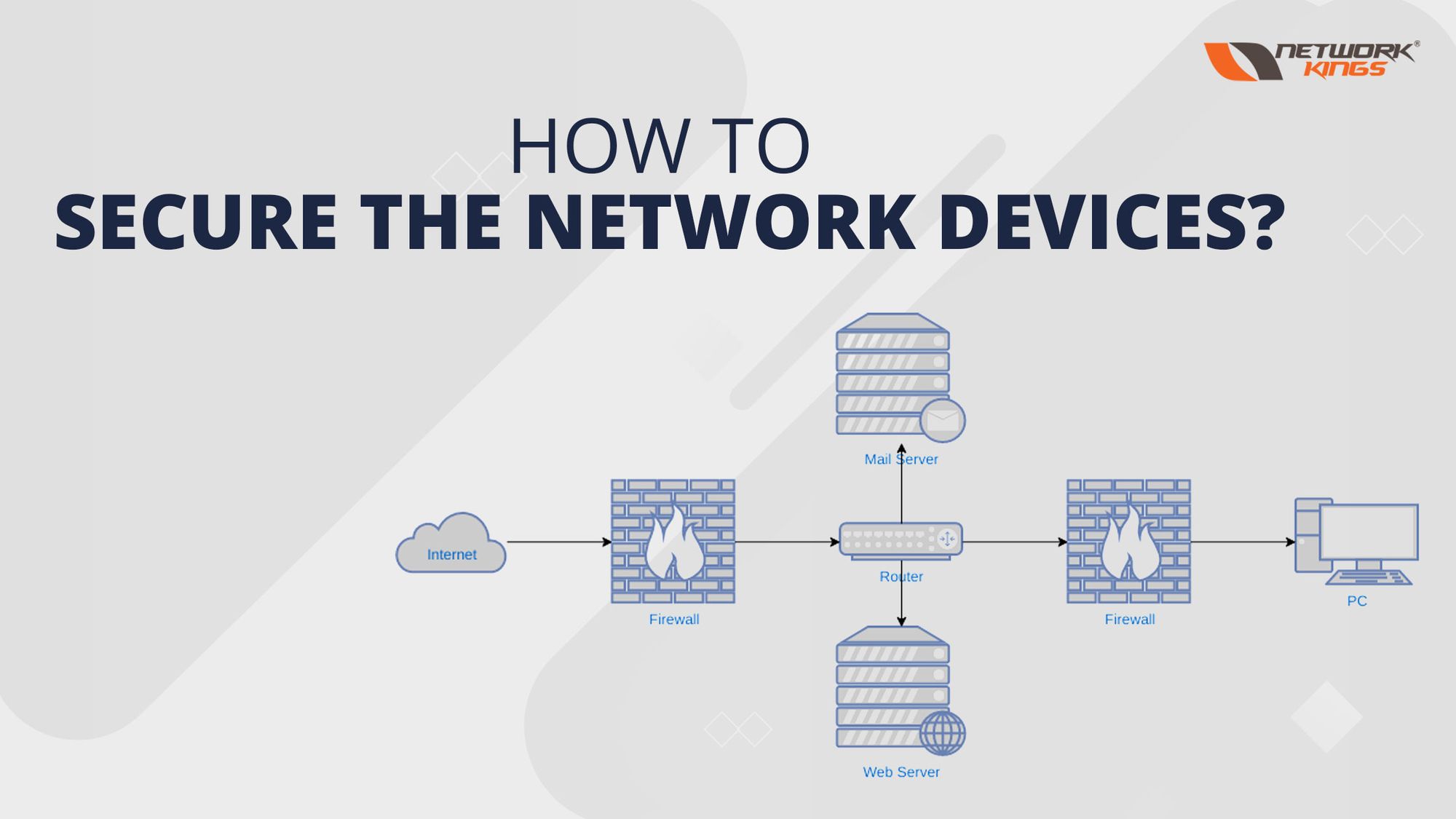
How To Secure The Network Devices Network Kings

Information Technology Inventory Template Fresh 7 It Inventory Templates Excel Templates Information Technology Conference Phone

Virtual Firewall Network Topology Download Scientific Diagram
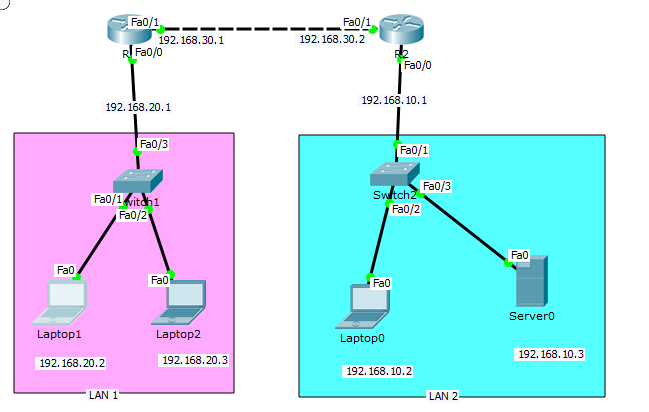
Comprehensive Ccna Interview Questions And Answers 2022

2 The Mobile Phone As A Router Bridge Download Scientific Diagram

A Network Of Firewalls And Routers The Firewall Filter And Routing Download Scientific Diagram

Dmz Tables 1 And 2 Show A Summary Of The Network Topologies And Download Scientific Diagram

Schema Of The Network Infrastructure Used In The Paper To Collect Download Scientific Diagram

Localization Of Ips On Layer 2 Switch Download Scientific Diagram

Netgear Smart Wifi Router R6350 Ac1750 Wireless Speed Up To 1750 Mbps Up To 1500 Sq Ft Coverage 20 Devices 4 X 1g Ethernet And 1 X 2 0 Usb Ports Amazon Ca Electronics

Solved No Internet When Routing Vlan Traffic To Vpn On Usg Openvpn Ubiquiti Community

Illustration Of The Proposed Framework With 20 Mv Cameras Download Scientific Diagram
The Proposed Wireless Lan Network With 20 Workstations Download Scientific Diagram